The modern workplace runs on connectivity. From HVAC systems and lighting controls to access management and energy monitoring, Integrated Facility Management (IFM) systems have transformed how organizations maintain their buildings. But this digital transformation comes with a hidden cost: cybersecurity risk.
- Majority of facility systems have unpatched vulnerabilities
- Dramatic increase in attacks on building systems
- Multi-million dollar average cost per breach
As facility management systems become more interconnected, they also become more vulnerable to cyber attacks. A breach in your building’s management system isn’t just an IT problem—it can compromise physical security, disrupt operations, and expose sensitive data.
What Integrated Facility Management Systems Depend on Today?
Modern IFM platforms operate on a complex web of interconnected technologies. Here’s what keeps them running:
- IoT Sensors: Thousands of connected devices monitoring temperature, occupancy, air quality, and more
- Cloud Platforms: Remote data storage and analytics accessible from anywhere
- Mobile Access: Real-time control through smartphones and tablets
- Third-Party Integrations: Vendor platforms for maintenance, energy analytics, and compliance
Key Insight: The average commercial building now has hundreds of connected devices, each representing a potential entry point for cyber attackers. This includes everything from smart thermostats to elevator controllers.
Why Integrated Facility Management Systems are Vulnerable to Cyber Threats?
Let’s be honest—building systems weren’t built with hackers in mind. Many were designed decades ago when physical isolation was the only security needed. Here’s what makes them such attractive targets:
Real-World Example: In recent years, major retail chains and hotel groups have experienced ransomware attacks through their HVAC contractor’s remote access portals. The attackers encrypted building controls across multiple locations, causing millions in damages and operational disruption for days.
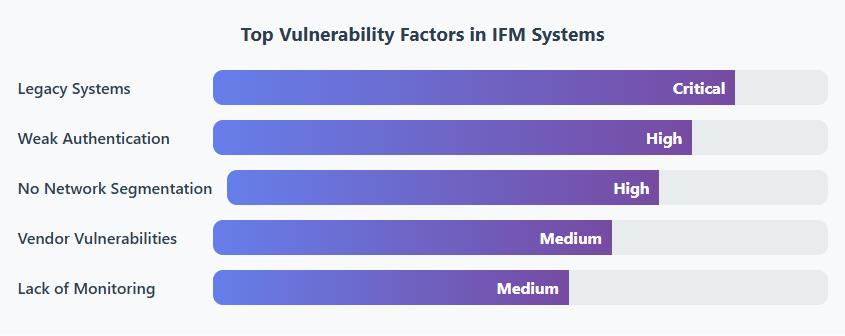
Key Cybersecurity Challenges in Integrated Facility Management
The threats are real, and they’re evolving. Here are the critical challenges facility managers face today:
- Lack of Visibility and Asset Inventory
Most organizations don’t even know what’s connected to their networks. Shadow IoT—devices installed without IT approval—creates massive blind spots. Can you protect what you can’t see? - Outdated and Unpatched Systems
Building automation systems often run on operating systems that vendors stopped supporting years ago. Applying patches requires downtime that nobody wants to schedule, leaving vulnerabilities open for months. - Insufficient Access Controls
Contractors from 2 years ago still have access. Default passwords like “admin123” are everywhere. Multi-factor authentication? What’s that? This is the reality in many facilities. - Inadequate Network Segmentation
Your HVAC system shares the same network as your financial databases. One compromised sensor can become a highway to your most sensitive data. - Limited Security Monitoring
Without proper monitoring tools, attacks can go undetected for weeks or even months. Many breaches in building systems remain undiscovered for extended periods, giving attackers plenty of time to cause damage.
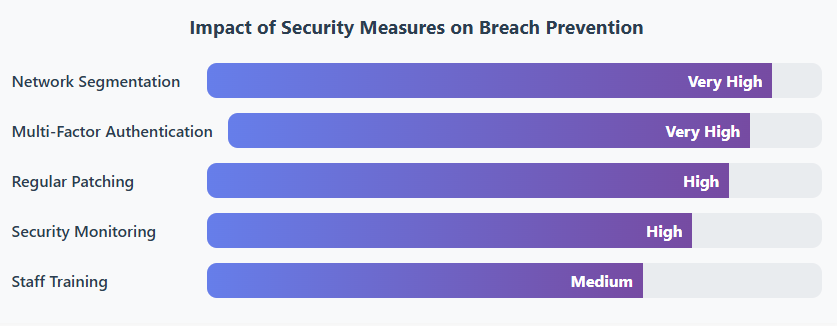
Cybersecurity Solutions for Integrated Facility Management Systems
Enough doom and gloom. Let’s talk solutions. Here’s your action plan for securing your IFM systems:
Network Segmentation: Your First Line of Defense
Think of it as creating separate “security zones” in your building. Your facility management systems should be on a completely different network from your corporate IT. Use VLANs and strict firewall rules to control what can talk to what.
Zero-Trust Architecture
Never trust, always verify. Every access request needs authentication, whether it’s from inside or outside your network
Regular Vulnerability Assessments
Quarterly scans + annual penetration testing = finding problems before hackers do
Security by Design
Evaluate vendors on security practices, require encryption, insist on regular updates
Endpoint Detection & Response
Monitor all building controllers 24/7 for suspicious behavior and unauthorized changes
Best Practices Facility Leaders Should Follow to Reduce Cyber Risk
Here’s your practical, actionable checklist for protecting your facility management systems:
- Create a Complete Asset Inventory
Document every single connected device. Include make, model, firmware version, network location, and who’s responsible. Update it quarterly—make it someone’s actual job responsibility. - Implement Strong Authentication
Complex passwords + multi-factor authentication + no shared accounts = basic hygiene. Eliminate default credentials immediately. Yes, that means changing “admin/admin” on every device. - Develop an Incident Response Plan
What happens when (not if) you get attacked? Who do you call? How do you safely shut down systems? Practice with tabletop exercises so everyone knows their role. - Provide Regular Security Training
Your facility team needs to recognize phishing emails, understand social engineering, and follow secure remote access procedures. Security awareness isn’t just for IT anymore. - Establish Vendor Management Protocols
Include security requirements in contracts. Assess vendors before integration. Require notification of breaches. Review access permissions regularly—don’t let old vendors retain backdoor access.
Why Cybersecurity must be part of every Integrated Facility Management Strategy?
Still think cybersecurity is just an IT problem? Think again. Here’s why it needs to be at the center of your facility management strategy:
The Real Consequences of Ignoring IFM Cybersecurity:
❌ A compromised HVAC system can shut down your entire operation
❌ Attackers could manipulate access controls to enable physical break-ins
❌ Ransomware can hold your building systems hostage
❌ Equipment damage from malicious commands costs millions
❌ Unsafe working conditions put employees at risk
Regulatory compliance is tightening up. GDPR, industry-specific standards, and emerging IoT security regulations now address building systems. Organizations that ignore facility management cybersecurity face fines, legal liability, and loss of certifications.
But here’s the positive spin: strong cybersecurity creates competitive advantage. Tenants, clients, and partners increasingly evaluate security practices when selecting buildings or service providers. Demonstrating security maturity can actually differentiate your organization and attract premium clients.
Conclusion
Integrated Facility Management systems have revolutionized building operations, but they’ve also created new cybersecurity responsibilities that facility leaders can’t ignore. The interconnected nature of modern building systems means that security must be built in from day one, not bolted on as an afterthought.
Take Action Today, start with these three immediate steps:
1️⃣ Conduct an asset inventory of all connected devices
2️⃣ Implement multi-factor authentication on all facility systems
3️⃣ Schedule a security assessment with a qualified professional
By understanding the unique vulnerabilities of IFM systems, implementing appropriate technical controls, and fostering a security-conscious culture among facility teams, organizations can protect their physical infrastructure without sacrificing operational efficiency.
The question isn’t whether to invest in cybersecurity for facility management—it’s whether you can afford not to.
Frequently Asked Questions(FAQs):
1. What are the biggest cybersecurity risks in Integrated Facility Management systems?
The biggest risks include outdated and unpatched systems, inadequate network segmentation, weak authentication, lack of visibility into connected IoT devices, and third-party vendor vulnerabilities. Many building systems use legacy protocols without encryption, making them easy targets for attackers.
2. How can facility managers improve cybersecurity without disrupting operations?
Start with network segmentation to isolate building systems, gradually deploy multi-factor authentication, conduct vulnerability assessments during scheduled maintenance, create comprehensive asset inventories, and provide regular staff training. These measures can be phased in to minimize disruption while significantly improving security.
3. Should Integrated Facility Management systems be on separate networks from corporate IT?
Yes, absolutely. Separate networks prevent attacks from spreading between facility and corporate systems. Use strict firewall rules to control communication between networks. This creates secure barriers while allowing necessary data exchange where needed.
4. What security features should organizations look for when selecting IFM vendors?
Look for encrypted communications, regular security updates without extended downtime, multi-factor authentication support, role-based access controls, and relevant certifications (ISO 27001, SOC 2). Vendors should have transparent security practices, proven incident response procedures, and willingness to undergo third-party security assessments.
5. How often should facility management systems undergo security assessments?
Conduct quarterly vulnerability scans and annual penetration testing by qualified professionals. Also perform security reviews when integrating new systems, after major configuration changes, or following any security incident. Use continuous monitoring tools (SIEM) for real-time threat detection between formal assessments.





































